Solidity is a powerful programming language used to write smart contracts on blockchain platforms like Ethereum. However, just like any other programming language, it has its vulnerabilities. One such vulnerability is block timestamp manipulation, which can be exploited by attackers to manipulate the timestamp of a block in order to compromise the integrity of a smart contract.
Block timestamp manipulation occurs when an attacker manipulates the timestamp of a block in order to trick a smart contract into executing a particular function or transaction. This can result in a loss of funds or a breach of data.
So, how can you protect your Solidity smart contracts from block timestamp manipulation? Here are some tips:
- Use
block.numberinstead of block.timestamp Instead of using block.timestamp to generate a timestamp, useblock.numberto generate a block number. This makes it harder for attackers to manipulate the timestamp, as they would need to manipulate the block number as well. - Use an
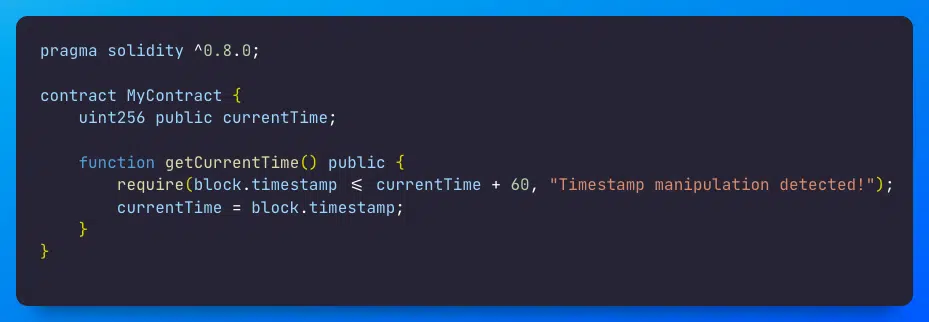
externalsource for timestamps Another way to prevent block timestamp manipulation is to use an external source for timestamps. This can be a trusted oracle or an off-chain service that provides a timestamp that cannot be manipulated by attackers. - Implement a time window for transactions Implementing a time window for transactions can also help prevent block timestamp manipulation. By setting a specific time window for a transaction to be executed, you can prevent attackers from manipulating the block timestamp to execute the transaction at an unexpected time.
- Implement security best practices Finally, it’s important to implement security best practices when developing your Solidity smart contracts. This includes using secure coding practices, conducting regular security audits, and keeping your contracts up-to-date with the latest security patches.
By following these tips, you can help protect your Solidity smart contracts from block timestamp manipulation and other vulnerabilities. It’s important to always be vigilant and stay up-to-date with the latest security threats in order to keep your contracts and your users safe.
Using Block Timestamp in a Smart Contract
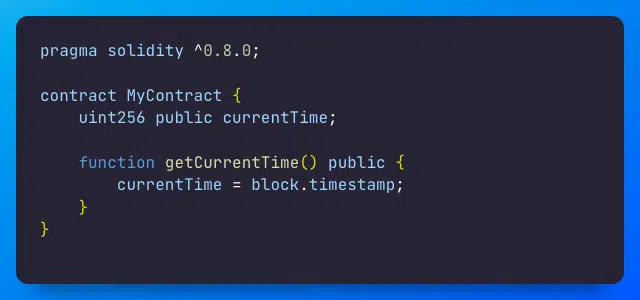
Limiting Execution Time Using Block Timestamp
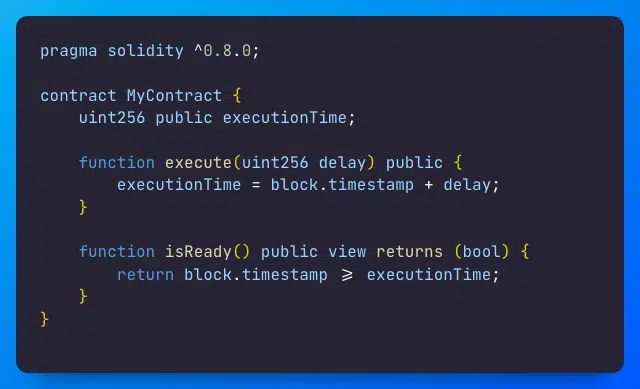
Protecting Against Timestamp Manipulation
Posted in Blockchain, Smart Contract, Solidity, Technologies





